Cybersecurity: Meaning & Definition
Cybersecurity is the combination of methods, processes, tools, and behaviors that protect computer systems, networks, and data from cyberattacks and unauthorized access. Although deeply rooted in technology, the effectiveness of cybersecurity also very much depends on people.
Human error, negligence, or lack of awareness can create vulnerabilities that cybercriminals exploit. By following best practices, staying informed, and adhering to security protocols, individuals play a crucial role in preventing breaches and keeping computer systems safe.
Why is cybersecurity important?
The rapid pace of digital transformation has changed how organizations conduct business and how people shop, work, and communicate, with e-commerce, remote collaboration, and cloud data storage becoming cornerstones of modern life. Beyond personal and business usage, critical infrastructure like gas pipelines, electrical grids, and other essential services are now managed online, making them vulnerable to cyberattacks.
As organizations and consumers increasingly entrust sensitive information to digital systems, the need for robust cybersecurity measures has never been greater. They not only protect this data, but also ensure the safety and reliability of services that power countless lives daily.
Cybersecurity challenges
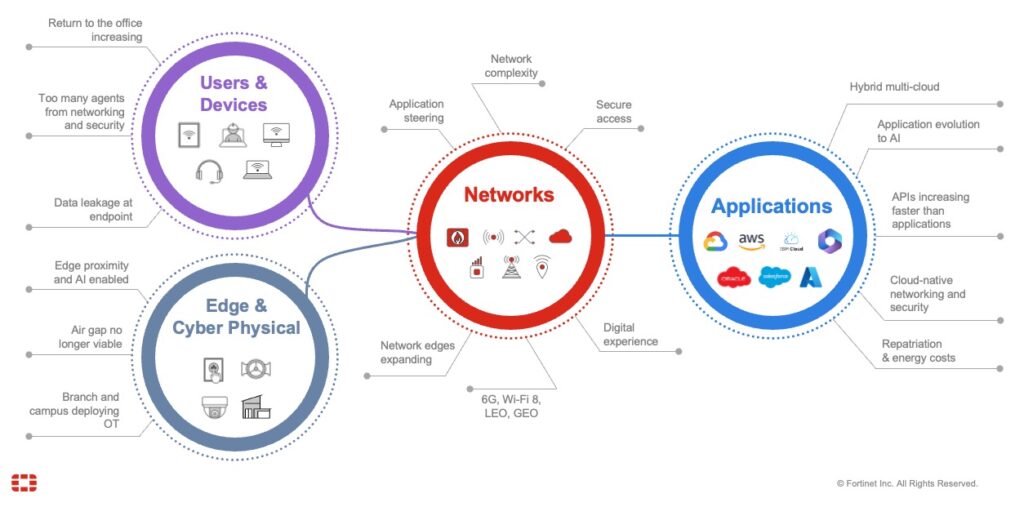
- Increasing complexity: Recent years have seen a notable uptick in digital acceleration with businesses adopting new technologies to stay competitive. However, managing and securing these investments has become much more complicated. Isolated point products from multiple vendors expand the attack surface and fragment the security posture. Consequently, enforcing consistent policies across the entire infrastructure is increasingly difficult.
- Evolving threats: With organizations exposed, cybercriminals are exploiting vulnerabilities at an unrelenting rate. Even worse, they’re employing increasingly sophisticated tactics to circumvent traditional protections and launch nuanced, multi-vector attacks. These threats are more difficult to detect, thus slowing response times and leading to devastating results.
- Outdated strategies: Traditional, siloed security solutions are no longer adequate for modern threats. Disconnected tools and manual processes leave security gaps open and delay real-time response, which can make all the difference during a cybersecurity incident. In an environment where conditions change rapidly, relying on outdated methods often means being unprepared for emerging challenges. This highlights the need for organizations to adapt their cybersecurity strategies to the new era of evolving threats and strengthen long-term resilience.
Top Cyber Threats Shaping Cybersecurity Platform Strategy
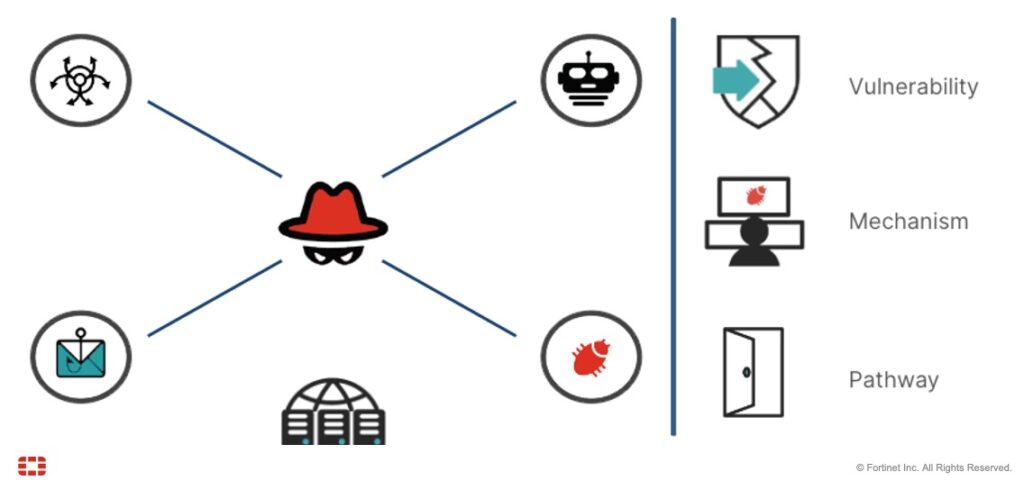
The “threat landscape” refers to the totality of potential cyber threats in any given context. That last part is important, as what’s considered a significant risk to one company may not necessarily be one to another.
Monitoring and analyzing the threat landscape is vital to achieving effective protection. Knowing your enemy allows you to better plan against their tactics. In cybersecurity, these enemies are called bad actors — people who try to exploit a vulnerability to steal, sabotage, or stop organizations from accessing information they’re authorized to use.
An attack vector is a mechanism or method the bad actor uses to illegally access or inhibit a network, system, or facility. Attack vectors are grouped into three categories: electronic social engineering, physical social engineering, and technical vulnerabilities (e.g., computer misconfigurations). When threat actors exploit an attack vector, the ensuing chain of events is called the pathway (or attack path).
Cyber threat examples
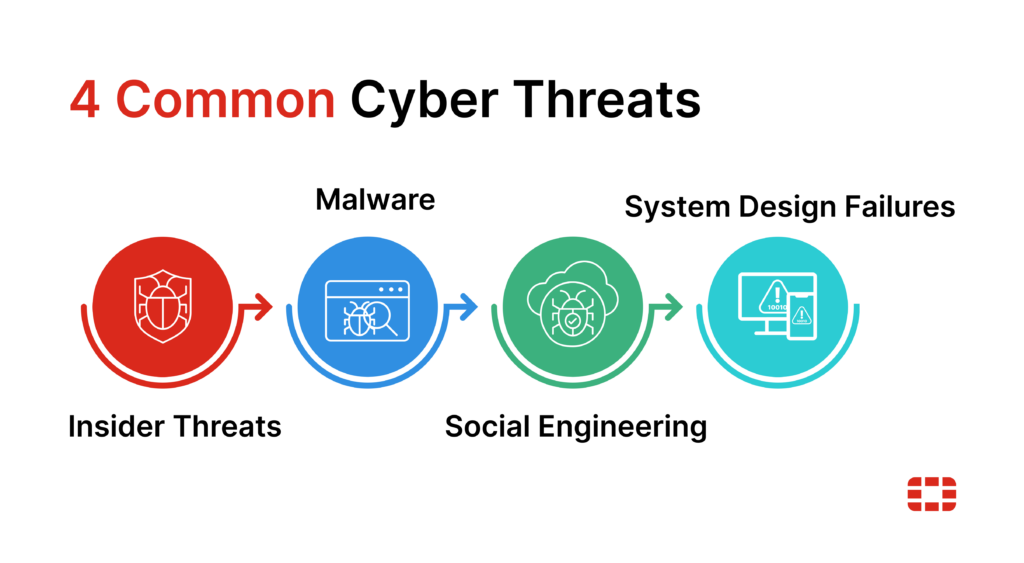
Insider threats
Not all cybersecurity incidents originate externally. Insider threats occur when individuals within an organization — employees, contractors, partners, etc. — intentionally or unintentionally compromise security. These events are especially dangerous because insiders often have legitimate and privileged access to sensitive information, making it easier to cause harm or expose data.
Insider threats come in two forms:
- Malicious insiders: These individuals intentionally exploit their access to steal data, sabotage systems, or leak confidential information. Motivations can range from financial gain to revenge or corporate espionage. For example, a disgruntled employee with access to critical systems might delete valuable data or sell trade secrets to competitors.
- Unintentional insiders: These threats arise when employees unknowingly create security risks through careless actions, such as falling victim to phishing attacks, using weak passwords, or mishandling sensitive data.
Malware
Malware, or malicious software, refers to any software program designed to harm computer systems, networks, or users. It can infect devices, steal data, or disrupt operations, making it one of the most common and impactful cyber threats.
Although it comes in many forms, malware typically falls into the following categories:
- Viruses: A virus attaches itself to a legitimate file or program and spreads to other systems when the infected file is shared or executed. Once activated, viruses can corrupt files, steal data, or damage systems.
- Trojan horses: Disguised as legitimate software, trojans trick users into downloading and installing them. Once inside the system, they create backdoors for attackers to steal data, install more malware, or take control of the device.
- Worms: Unlike viruses, worms can replicate themselves and spread across networks without any human interaction. Worms often exploit vulnerabilities in operating systems, quickly infecting large numbers of devices and causing widespread damage.
- Botnet: A botnet is a network of compromised devices, often controlled remotely by cybercriminals. These “bots” can launch large-scale strikes such as distributed denial-of-service (DDoS) attacks, which overwhelm systems with illegitimate traffic to take them offline.
- Ransomware: This form of malware encrypts the victim’s files or locks them out of information systems, demanding payment in exchange for their safe return. Ransomware attacks can severely disrupt operations by holding critical data hostage until the ransom is paid.
Social engineering
Social engineering is a type of cyberattack that relies on human interaction to manipulate individuals into revealing sensitive information or performing actions that compromise security. Rather than exploiting software vulnerabilities, social engineering preys on human psychology, making it one of the most challenging threats to prevent.
Frequent examples include:
- Phishing: Attackers send deceptive emails or messages that appear legitimate, tricking individuals into clicking malicious links, providing login credentials, or downloading malware. Phishing is one of the most widespread social engineering tactics, often targeting employees with privileged accounts.
- Fraud: This involves tricking individuals or organizations into sharing confidential information or making unauthorized payments. Attackers may pose as trusted entities, such as vendors or executives, to deceive their targets.
- Scams: These attacks involve convincing individuals to provide sensitive information or transfer money under false pretenses, often by creating a sense of urgency or fear. Common scams include fake tech support calls or lottery scams.
- Influence campaigns: Attackers manipulate public opinion or decision-making processes through misinformation or disinformation, often using social media. These campaigns can destabilize businesses or even governments by spreading false information to large audiences.
System design failure
A system design failure is a security flaw within a computer system or application that a bad actor exploits to gain access. For instance, coding errors and misconfigurations during the development process may leave gaps in an application’s security posture. If the application isn’t updated after deployment, hackers could leverage these open vulnerabilities to their advantage.
One of the most common ways cybercriminals do so is through a structured query language (SQL) injection. SQL is a standard language used to query databases. Bad actors try to insert an SQL query into regular input or form fields, passing it to the application’s underlying database. This can lead to unauthorized access to sensitive data, corruption, or even a complete database takeover.
Considerations for a cybersecurity platform
Digital transformation may have helped organizations push forward, but it’s also added immense complexity to an already complex environment. Each innovation only further stretches the attack surface, challenging teams to manage a mixed bag of technologies that don’t always work together.
Point solutions and siloed tools have led to a lack of coherent management, orchestration, and enforcement — and with that, an increasingly strained network. Without visibility, the sprawling attack surface is more vulnerable than ever before. That’s why enterprises need a comprehensive and unified approach where networking and security converge to protect the entire IT infrastructure and are complemented by robust security operations technologies for comprehensive threat detection and response.
How do you choose the right approach? Here are five essential questions enterprises should consider:
- Can the approach converge key networking and security functionalities into a single solution to reduce complexity and improve protection?
- Can it work with solutions from multiple vendors through open APIs and other capabilities?
- Does it encompass all potential attack vectors and edges, including those not yet deployed?
- Is it supported by a single source of threat intelligence derived from its in-house threat research and collaboration with key members of the cybersecurity community?
- Does it support a single-pane-of-glass management philosophy?
Ultimately, only an integrated approach that leverages both convergence and consolidation can mitigate modern cybersecurity’s most daunting challenges. With this approach, enterprises can leverage a full range of capabilities and protect all their critical assets from current and emerging threats.
Cybersecurity Risk Statistics: Hidden Costs and Organizational Impact
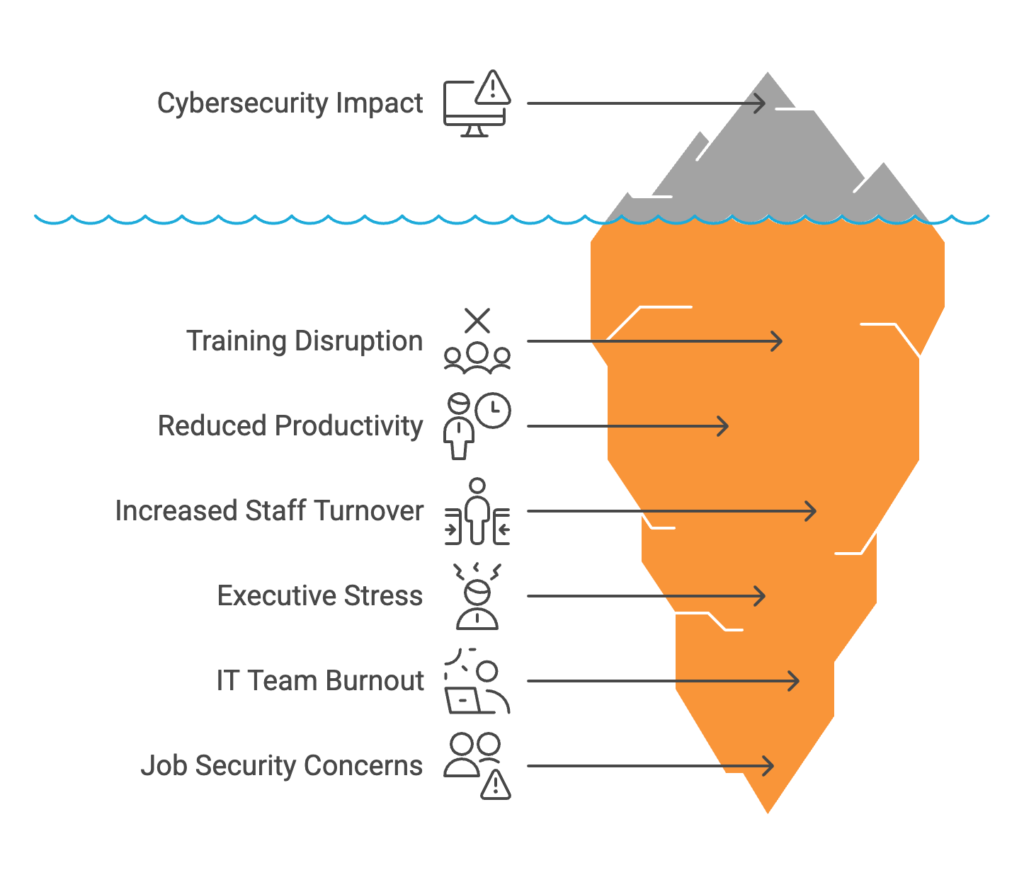
Cybersecurity risks can disrupt an organization’s operations, impacting productivity and efficiency. However, operational downtime is just a surface-level consequence. The real impact goes much deeper. It begins with hampered operations and leads to financial losses. Moreover, hackers can misuse stolen data, resulting in regulatory fines, penalties, and damage to the organization’s reputation. This, in turn, can cause loss of customer trust and hinder long-term growth.
Here are a few key statistics to help understand the real-time impacts.
Financial & operational consequences of cyberattacks
Cyberattacks can damage enterprises by causing downtime, data loss, and financial setbacks.
- According to the Cost of a Data Breach Report, the average breach results in USD 2.8 million in lost business.
- Anne Neuberger, US Deputy National Security Advisor for cyber and emerging technologies, reveals that the annual average cost of cybercrime will reach $23 trillion in 2027.
- According to CompTIA, the global cybercrime costs will hit $10.5 trillion by 2025, marking a 10% year-over-year increase.
Beyond immediate financial loss, responding to breaches adds hidden costs. However, organizations using AI and automation in security saved an average of $2.22 million over those that didn’t.
Reputational & compliance risks
Reputational damage is an indirect loss that significantly increases overall impact, often far exceeding the initial financial cost.
- Public companies, particularly in the financial sector, are highly vulnerable. They account for nearly one‑fifth of all cyberattack incidents, with banks being the most exposed.
- According to Statista, most ransomware cyberattacks happen because of phishing attacks (54%), poor cybersecurity practices (27%), lack of employee training (26%), and visiting malicious websites (14%).
These incidents can expose sensitive data or disrupt services, leading customers to lose trust in the organization’s ability to protect their information. This can ultimately harm the brand’s reputation and credibility.
Cybersecurity risks for SMBs vs. enterprises
While large enterprises often are targeted, SMBs are equally at risk, often with fewer resources to recover. Today, hackers target smaller organizations with lower cybersecurity maturity, resulting in significant disruption and business continuity issues.
According to Mastercard’s global SMB cybersecurity study, nearly one in five SMBs that suffered a cyberattack filed for bankruptcy or had to close. This reflects the growing focus of cybercriminals on smaller businesses.
Workforce disruption
As stated, cyberattacks lead to employee downtime, hindered workflows, and productivity issues. The 2023 ransomware attack on a US IT cloud provider caused outages at 60 credit unions simultaneously. It disrupted thousands of employees and customers.
Supply chain risk
Cyberattacks targeting supply chains have become more frequent and damaging. According to a 2024 global survey by Statista, financial loss was the most common consequence of supply chain attacks, followed by data breaches and reputational damage.
9 Building Blocks of a Comprehensive Cybersecurity Strategy
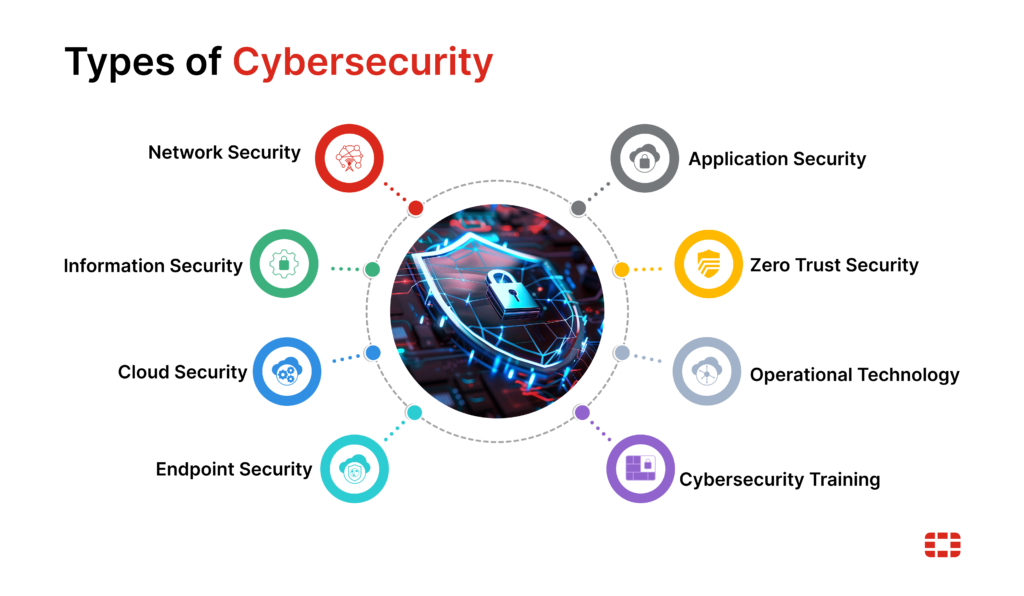
Cybersecurity isn’t a singular solution but rather a convergence of multiple approaches. They work together in concert to protect users, systems, networks, and data from all angles, minimizing risk exposure.
By combining these layers of protection, businesses can create a more resilient defense against cyber threats of all shapes and sizes.
1. Network security
Network security safeguards communication infrastructure, including devices, hardware, software, and communication protocols. It protects data integrity, confidentiality, and availability as information travels over a network and between network-accessible assets, such as a computer and an application server.
Network security also encompasses a broad collection of technologies, policies, people, and procedures. These focus primarily on preventing known threats from infiltrating the communication infrastructure.
For example, firewalls filter incoming and outgoing traffic, acting as a first line of defense by identifying familiar attack types, suspicious activity, or unauthorized access attempts based on pre-defined rules. The idea is that firewalls already know what to expect and have the capability to block these threats before they can cause harm.
However, network security tools must also include an element of detection. Firewalls and other network security solutions must be able to identify unfamiliar or new threats and, through integration with other systems, respond appropriately to mitigate the risk. Within this context, understanding the distinction between network security vs cyber security provides clarity on where each discipline contributes to an organization’s broader security strategy. To strengthen this posture, organizations also need continuous visibility into emerging network security threats and vulnerabilities, ensuring protections evolve alongside new attack techniques.
2. Information security
Information security, or InfoSec, is the practice of protecting information. It refers to the tools and processes for preventing, detecting, and remediating threats to sensitive information, whether digitized or not.
InfoSec is closely related to data security — a subset that specifically protects digitized data stored in systems and databases or transmitted across networks. Both disciplines share three primary objectives:
- Confidentiality: Ensuring confidential information remains a secret.
- Integrity: Protecting information from being altered, manipulated, or deleted.
- Availability: Making information readily accessible to those who need it.
Therefore, information and data security solutions safeguard against unauthorized access, modification, and disruption. A key aspect of both disciplines is the need to scrutinize information, allowing organizations to classify it by criticality and adjust policies accordingly.
For example, data loss prevention (DLP) tools automatically discover and classify data as it’s created. They also monitor, detect, and prevent unauthorized data sharing or extraction, ensuring valuable information remains secure within the organization.
3. Cloud security
Cloud security refers to the technologies, policies, and procedures that protect data, applications, and services hosted in private and public cloud environments. It ensures sensitive information is safe from data breaches and other vulnerabilities, whether stored in public, private, or hybrid clouds. Cloud security solutions are often versions of on-premises solutions that are specifically for the cloud. As such, cloud security can be a seamless extension of an organization’s network security.
One of cloud computing’s biggest security challenges is providing users with safe, frictionless access to their most essential applications. Cloud-based services are available off-premises, but the devices used to reach them are typically unprotected.
Organizations often mitigate security risks using identity and access management (IAM), a key strategy that ensures only authorized users can access specific resources. IAM solutions are not limited to cloud environments; they are integral to network security as well. These technologies include robust authentication methods, multi-factor authentication (MFA), and other access controls, all of which help protect sensitive data and systems across both on-premises and cloud-based infrastructures.
4. Endpoint security
Endpoint security focuses on protecting the devices that serve as access points to an organization’s network, such as laptops, desktops, smartphones, and tablets. These devices, or endpoints, expand the attack surface, providing potential entry points for cybercriminals to exploit vulnerabilities and infiltrate the broader infrastructure.
To reduce risk, organizations must apply the right security solutions to each endpoint, ensuring protection is tailored to the specific device and its role in the network. For example, laptops used by remote workers may require antivirus software and multi-factor authentication to prevent malware attacks or unauthorized access.
A related subset of endpoint security is mobile security, which specifically addresses the vulnerabilities of mobile devices. As employees increasingly use smartphones and tablets for work, securing these endpoints becomes critical to protecting the entire network. Security solutions, such as mobile device management, help organizations manage and secure these devices, preventing them from becoming weak links in the cybersecurity chain.
5. Application security
Application security refers to the technologies, policies, and procedures at the application level that prevent cybercriminals from exploiting application vulnerabilities. It involves a combination of mitigation strategies during application development and after deployment.
For instance, a web application firewall (WAF) monitors and filters traffic between applications and the outside world, blocking malicious activity like code injections or cross-site scripting attacks. With robust application security, organizations can ensure their software remains protected against threats that target the app and the sensitive data it processes and stores.
6. Zero trust security
Zero trust is a modern cybersecurity model that assumes no user or system, whether inside or outside the network, is automatically trustworthy by default. Instead, organizations continuously verify access to data and resources through strict authentication protocols.
Unlike traditional security models, which take a “castle-and-moat” approach, zero trust monitors more than just the perimeter. It enforces granular security controls across all endpoints, applications, and users, preventing unauthorized lateral movement. In other words, users can’t freely roam inside the network without reconfirming their identity whenever they request access to a particular resource.
7. Operational technology (OT) security
OT security, which uses the same solutions and techniques as IT environments, protects the safety and reliability of system technologies that control physical processes in a wide range of industries. This includes critical infrastructure like manufacturing systems, energy grids, and transportation networks, where a security breach could result in significant damage, but has come to include banking systems and others as well.
Traditionally, security in these environments wasn’t necessary. Most operational technologies weren’t connected to the outside world, so they didn’t require protection. Now, as IT and OT converge, they’re increasingly exposed to malicious activity.
IoT security also focuses on protecting connected devices — but on a broader scale. IoT devices range from sensors in industrial equipment to smart thermostats in homes. Because they’re web-enabled, these access points expand the attack surface. Plus, since they often have limited security capabilities, they’re vulnerable entryways for cybercriminals to exploit.
To address this, IoT security solutions focus on device authentication, encryption, and network segmentation, ensuring secure communication and preventing unauthorized access. Organizations must monitor these devices closely and implement strong access controls to minimize risks.
The inclusion of IoT security into the traditional industrial world of OT has introduced a new concept: cyber-physical systems and their security.
Cybersecurity training & certification
Cybersecurity awareness & skills development
Because people are the most vulnerable part of the cybersecurity equation, organizations must take measures to mitigate their human factors. The best way to achieve this is through end-user education — teaching the people who use technology to defend computer systems, networks, and the information therein.
At a minimum, cybersecurity awareness training ensures users can recognize and respond to common threats, like phishing, malware, and social engineering. Comprehensive cybersecurity training programs for employees go beyond basic password hygiene, covering specific risks relevant to the organization’s industry.
Many companies are turning to online platforms to make education more accessible, offering flexible cybersecurity training courses that can be completed remotely. For those seeking to deepen their expertise, cybersecurity training certification programs offer more advanced skills and recognition of their knowledge, helping employees stay current with evolving threats and security practices.
All of these efforts are to change what traditionally has been the weakest link in the chain — the human element — into an effective front line of defense and early warning system.
Cybersecurity certification programs
Cybersecurity certifications provide a structured way for professionals, regardless of experience level. Most importantly, investing in certification programs helps organizations close internal skill gaps, reduce the risk of breaches, and future-proof their cybersecurity workforce.
In fact, organizations are recognizing the significance of certified talent. According to Fortinet’s 2024 Global Skills Gap Report:
- 91% of organizations prefer hiring candidates with certifications.
- 90% of business leaders are willing to fund employee certification training.
- 95% of those with certified teams report a positive impact on performance.
Managed cybersecurity services
Managing cybersecurity can be complex and resource-intensive for many organizations. However, businesses have several options for addressing these challenges. They can choose to handle cybersecurity in-house, partner with a trusted managed security service provider (MSSP) to monitor and manage their security infrastructure, or adopt a hybrid approach that combines both internal resources and external expertise. Each option offers different benefits depending on the organization’s needs and resources, allowing them to tailor their security strategy effectively.
MSSPs offer scalable solutions that provide organizations with access to advanced cybersecurity technology, threat intelligence, and expertise without requiring them to build and maintain their own infrastructure. For example, managed services can range from basic services such as a managed firewall to more sophisticated services such as:
- MDR: Managed detection and response is a service that integrates a team of Security Operations Center (SOC) experts into your workforce. MDR provides these skilled professionals to continuously monitor user behavior and act when a threat is detected, focusing primarily on endpoint protection.
- XDR: Extended detection and response goes beyond MDR, taking a software-based approach to secure all layers — not just endpoints. It integrates MDR procedures across multiple environments to reduce the mean time to detect and protect the entire attack surface.
Whether a business lacks the resources for an in-house security team or simply wants to enhance its existing capabilities, managed security services offer a cost-effective and comprehensive solution.
Strategic Cybersecurity Tools and Technologies for the Modern Enterprise
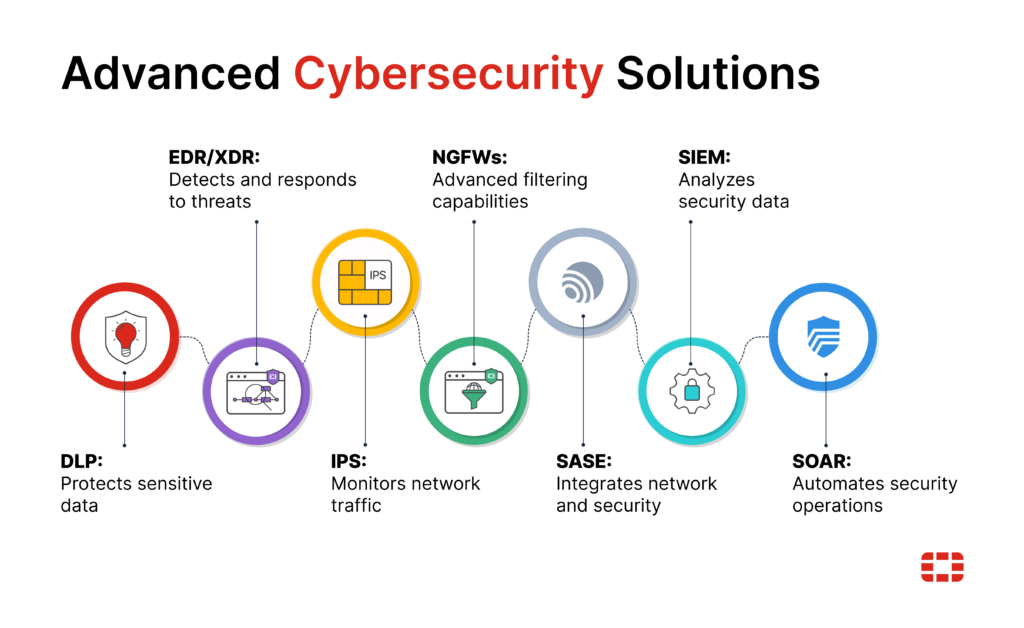
Advanced cybersecurity solutions provide comprehensive protection against sophisticated threats. These solutions utilize cutting-edge technologies like artificial intelligence, machine learning, and behavioral analysis to detect, prevent, and respond to cyberattacks in real-time. By implementing advanced cybersecurity solutions, organizations can proactively mitigate risks, strengthen their security posture, and safeguard their critical assets from evolving cyber threats.
Data loss prevention (DLP)
DLP tools monitor and control the flow of sensitive data across the network. They help safeguard customer data and proprietary information, detecting and preventing unauthorized attempts to share or extract it.
Endpoint detection and response (EDR)
An EDR solution continuously monitors devices for signs of malicious activity. By detecting and responding to incidents in real time, it mitigates the risk of an affected endpoint impacting the rest of the network.
Intrusion prevention systems (IPS)
IPS solutions detect and block known and suspected threats by analyzing traffic for signs of malicious activity. They protect against threats such as zero-day exploits and ransomware, stopping these risks through automated response procedures before they can impact the network.
Next-generation firewalls (NGFWs)
NGFWs go beyond traditional firewalls by incorporating advanced features like deep packet inspection and application awareness. They monitor and control traffic at a more granular level, enabling enterprises to block advanced malware and encrypted attacks. NGFWs help secure the network perimeter while providing greater visibility into network activity — key when dealing with today’s sprawling attack surfaces.
Secure access service edge (SASE)
SASE combines network security functions with wide area networking (WAN) capabilities into a single cloud-based service. By converging security and networking, SASE helps organizations protect their hybrid environments, including remote users’ endpoints and branch offices, ensuring consistent security policies and reliable access to resources.
Security information and event management (SIEM)
SIEM systems aggregate and analyze security data across the network to detect suspicious patterns. By providing unified visibility and generating real-time alerts, SIEM helps enterprises quickly identify potential incidents and respond proactively to mitigate.
Security orchestration, automation, and response (SOAR)
SOAR platforms streamline and automate the incident response process. By integrating with SIEM and other security tools, SOAR automates data collection and response execution, reducing manual effort and improving response times.
Emerging Trends Driving Cybersecurity Forward
As the cyber threat landscape continues to evolve, understanding cybersecurity trends for 2025 becomes increasingly crucial. This can help organizations implement the right strategies and training programs and take proactive measures to stay ahead of threats.
The evolving landscape of cybersecurity
- AI-powered cyber threats: Today, hackers are misusing AI tools for phishing attacks, malware, and deepfakes.
- Insider threats in the remote era: Remote work environments increase the risk of insider threats, often through compromised credentials.
- Zero-day exploits on the rise: Zero-day attacks are targeting unknown vulnerabilities before they can be patched.
- Ransomware-as-a-service (RaaS) evolution: RaaS makes it easier for low-skilled attackers to launch ransomware campaigns.
- Manufacturing and industrial IoT: IT and OT connectivity in manufacturing opens up new vulnerabilities through outdated firmware or insecure devices.
The transformative role of AI in cybersecurity strategy
AI empowers cybersecurity professionals by helping them detect, prevent, and mitigate threats proactively. The right tools help identify cyberattack patterns, monitor real-time network behavior, and flag anomalies like suspicious logins or IoT traffic. AI strengthens defenses by isolating threats, predicting vulnerabilities, and improving user authentication through behavior analysis.
Besides, AI powered cybersecurity solutions support threat attribution, filter phishing and spam, and foster collaborative threat intelligence sharing. This helps organizations stay ahead of evolving, AI-powered cyber risks.
10 Essential Cybersecurity Best Practices
There are many ways organizations can improve their security posture. Here are 10 best practices that won’t only enhance short-term defenses, but strengthen long-term resilience:
- Use frequent, periodic data backups: Organizations should regularly back up data to ensure that, if an attack occurs, they can quickly restore systems without significant loss.
- Implement multi-factor authentication: MFA adds an extra layer of security by requiring users to verify their identity through a combination of “who they are” — username and password — with something they know such as a one-time code. This reduces the risk of unauthorized access. MFA is one of the most effective defenses against credential theft.
- Provide ongoing cybersecurity training: Ongoing cybersecurity awareness training helps staff recognize and respond to suspicious activity, minimizing human vulnerability.
- Use proper password hygiene: Strong password policies should require long, complex passwords, changed regularly, rather than short, easily guessed ones. Organizations must also advocate against reusing passwords across platforms to prevent lateral movement and data exfiltration.
- Leverage encryption software: Sensitive data must be protected both at rest and in transit. Encryption helps safeguard confidential information by obfuscating its contents and rendering it unreadable to unauthorized parties, even if it’s intercepted or stolen.
- Regularly update software: Outdated systems often contain vulnerabilities that cybercriminals can exploit. Regularly updating applications and patching security flaws ensures they have the latest protections. An endpoint protection agent can monitor operating systems and applications and notify the user of needed updates.
- Limit user privileges: The zero trust model advocates for the principle of least-privileged access. This means users only have access to the resources necessary for their roles, thus minimizing the potential damage if their accounts are compromised.
- Develop an incident response plan: A clear and tested plan is critical during an active security threat. It should include steps for containment, mitigation, communication, and recovery, ensuring the organization can quickly address and respond to an attack.
- Segment the network: Segmentation is a strategy that divides the larger network into smaller isolated pieces. This ensures the impact of a breach is limited in scope, preventing bad actors from moving laterally to harvest more data.
- Conduct regular security audits: Businesses should periodically review their cybersecurity measures to identify weaknesses and gaps. Proactively testing defenses can help uncover vulnerabilities before attackers exploit them, allowing teams to strengthen the overall security posture.
Also read through this elaborate checklist containing cybersecurity tips for SMBs.
How Fortinet Can Help
Fortinet’s cybersecurity platform, the Fortinet Security Fabric, is a comprehensive solution that integrates multiple security products and services into one unified infrastructure. To help, the different technologies of the Security Fabric are grouped into three key pillars: Secure Networking, SASE, and Security Operations.
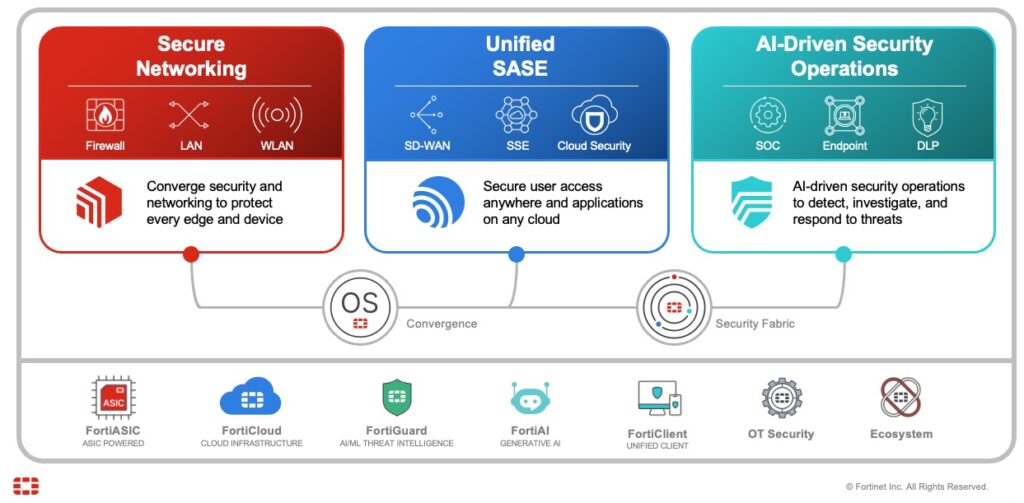
- Secure Networking: Fortinet offers a wide array of firewalls, switches, and wireless access points, all tightly integrated and managed through a single pane of glass. This allows for consistent security policies and simplified management across your entire network.
- SASE: Fortinet’s secure access service edge (SASE) solution combines networking and security functions in the cloud to deliver secure, high-performance access for remote users and branch offices. This eliminates the need for backhauling traffic to a central location, improving performance and reducing latency.
- Security Operations: Fortinet’s Security Operations solutions provide centralized visibility and control over your security posture. This includes tools for security information and event management (SIEM), security orchestration, automation and response (SOAR), and extended detection and response (XDR). These tools help you to detect, investigate, and respond to threats quickly and efficiently.
Rising cyber threats put your cloud, data, and applications at risk—stay protected with scalable security. Discover Fortinet cybersecurity solutions.
